Maintaining foothold is one of the key objectives of an adversary. Detecting that foothold is one of your key objectives as a forensicator! A few techniques which these adversaries for Persistence make use of rely on the Windows Registry - that’s our blog for today.
A Brief Overview of the Registry
The ‘Windows Registry’ is a central, hierarchical database of keys and values. These key-value pairs hold some of the most important configurations and settings which are then used by software, hardware devices, and the operating system itself.
Where is it stored?
The system-wide registry settings are stored in:
C:\Windows\System32\Config
Similarly, each user on the computer has its own copy of the user-specific register (or keys) which is stored in:
C:\Windows\Users\{UserName}\NTUSER.dat
However, you can’t edit these files yourself. Windows does provide a solution to this issue, which is ‘Regedit’, an application that can help you play around with your registry keys and values. Though here’s a disclaimer: You shouldn’t fool around with it unless you know what you’re doing. Small changes can be grave and likewise, if not taken properly. For the same reasosn, you should also have backups to ensure smooth recovery in case a problem does arise.
Open up regedit and give it a look. On the left pane, you have ‘groups’ of keys which have sub-nested keys in them with several values set in them. These groups, like ‘HKEY_CLASSES_ROOT’, are called ‘Hives’. What is a hive? A hive is a logical group of keys, sub-keys, and their values. These values are loaded into the memory and utilized by the operating system upon user logon.
 The left pane shows a few hives, the right pane shows its values
The left pane shows a few hives, the right pane shows its values
Though the same hive is loaded when an old user logs in, a new hive is created for new users. This new, separate file, is called the ‘user profile’ hive which is stored in the NTUSER.dat file in the User’s directory. This separate file consists of settings which are specific to that user and are used to load applications, configure them, setup network connections, printers, and more.
The following hives are present in every Windows setup by default:
| Registry Hive | Description |
| HKEY_CLASSES_ROOT | File extension association information (links to HKLM\Software\Classes) |
| HKEY_CURRENT_USER (HKCU) | User settings for currently logged-in user (links to HKEY_USERS{SID}) |
| HKEY_LOCAL_MACHINE (HKLM) | Stores all system-wide settings and configurations |
| HKEY_USERS | Stores the data for all users who exist on the system |
| HKEY_CURRENT_CONFIG | Information for the current hardware configuration (HKLM\SYSTEM\CurrentControlSet\Hardware Profiles\Current) |
Adding in New Keys and Values
When working with the registry, you might also want to create new keys and set their values accordingly. When doing so in regedit.exe, you can head over the key you’d like to create the subkey in. Then, rigth click and press the “New” and “Key” buttons to setup a new key. It won’t have any values by default.
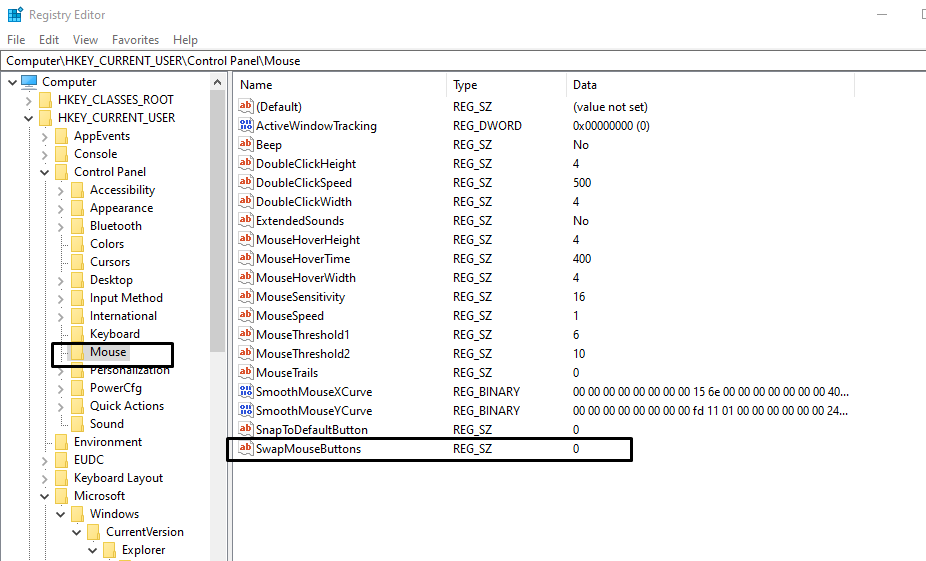 Left pane shows the keys, right has the values, whereas the ‘HKEY’ ones are the hives
Left pane shows the keys, right has the values, whereas the ‘HKEY’ ones are the hives
In the right pane, right click and select a value that you’d like to set up. Here’s a brief description of the values:
| Value Type | Value Description |
| String | Contains human-readable strings with alphanumeric characters. Indicated by the phrase ‘REG_SZ’ with a red symbol stating ‘ab’ |
| Multi-string Value | Contains a list of values rather than a single-line text. Indicated by the phrase ‘REG_MULTI_SZ’ with a red symbol stating ‘ab’ |
| Expandable String Value | Hold variables whose actual value is used by the OS at the time of execution or need. Indicated by the phrase ‘REG_EXPAND_SZ’ with a red symbol stating ‘ab’ |
| Binary Values | Contain binary values only. Indicated by ‘REG_BINARY’ with a blue icon containing binary numerics |
| DWORD (32-bit) and QWORD (64-bit) | Binary or hexa-decimal numbers used to satisfy the bit length of the value. A word equates to ‘16-bits’. Double word and Quad word are multiplied by 2 and 4, respectively. Indicated by ‘DWORD’ and ‘QWORD’ with a blue icon containing binary numerics |
That’s enough introduction to the Registry. Let’s dive in to some interesting keys and see how the Registry can be an asset to a malicious actor!
Persistence and the Registry
Persistence is a tactic which is followed by adversaries to maintain their foothold on a compromised machine. Under the tactic, several techniques exist which can help the adversary complete the objective - persist across system reboots, credential changes, or shutdowns. The purpose of this article is to discuss the achievement of persistence via Registry. Let’s get straight to discussing some Registry key, and their actual purpose, versus what the adversary can do.
Here’s a non-exclusive list of some of the most common registry values/locations which are targeted by malware:
Boot Keys
HKLM\SYSTEM\ControlSet002\Control\Session Manager\BootExecute
The Session Manager (ssms.exe) manages the sessions for each of your users in the Windows environment. After that, the WinLogon process starts which is spawned by the Windows Subsystem. The key I’ve mentioned above should always point to autochk.exe or authochk as it’s used to verify the integrity of the disks before the startup. If there are other values, the malware will be loaded along-side the autochk executable, and run for the entirety of the systems’ uptime.
If you’ve visited the value in your registry, it’s a “REG_MULTI_SZ” which allows it to accept a list of values; hence a easy target for malware to add themselves here.
User Log-on
HKLM\Software\Microsoft\WindowsNT\CurrentVersion\Winlogon\UserInit
HKCU\Software\Microsoft\WindowsNT\CurrentVersion\Winlogon\Shell
HKLM\Software\Microsoft\WindowsNT\CurrentVersion\Winlogon\Shell
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\IniFileMapping\system.ini\boot
The UserInit key is used by Windows to launch login scripts for the user. Initially, it points to userinit.exe, which then launches the Shell for Windows, explorer.exe. If the userinit.exe is replaced by the malware, that script or executable will be able to take over the login process. Similarly, the Shell key points to explorer.exe. It shouldn’t be anything other than that. Though these are String values so identifying changes should be easier. The last key we’ve mentioned in our list, the Shell key in here should also point to WinLogon only. Here’s the screenshot for that:
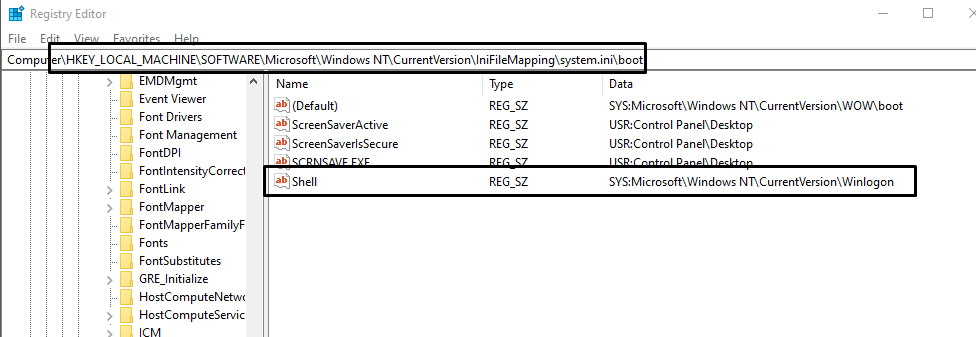
Run/RunOnce Keys, ASEPs, and Startup:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run
HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce
HKLM\Software\Microsoft\Windows\CurrentVersion\Run
HKLM\Software\Microsoft\Windows\CurrentVersion\RunOnce
HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunServices
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunServicesOnce
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce\Setup
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services
The Run and RunOnce keys are used to launch programs whenever a user logs on to the system, hence fall under AutoStart Extension Points (ASEPs). The Run key will launch the program on every user logon, whereas the RunOnce key only executes once and then, the key is deleted. If it fails, the computer won’t run it again in the case of RunOnce keys. However, you can change this behavior by using a “!” in front of your value so it waits until the command or execution of the program has ended and only then is the key deleted.
Malware use these keys regularly and are the most over-used keys, simply because of their ease-of-use and purpose. Monitor these keys to make sure no executable is being loaded (without your permissions of course, I only have my Antivirus loading here).
Most services are required to run at boot time. The RunServices and services and relevant keys are used to start up background services such as the “Remote Registry Service”. They’re vital to your system’s performance (and very likely to be targeted by the malware!).
Mind you, if the malware fails to gain admin privileges, it won’t load itself into the Run keys of HKLM. Rather, it’ll modify the HKCU keys.
Startup Keys
HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
Windows stores each user’s personal folders in the keys I’ve identified above. These will include your music, documents, downloads, etc. and other folders. However, malware can change this behavior to load a malicious executable rather than (let’s say you wanted to open up the Music folder) the intended folder.
AppInit DLLs
HKLM\Software\Microsoft\WindowsNT\CurrentVersion\Windows\AppInit_DLLs
Several DLL files are loaded by the User32.dll file, which is responsible for providing the core functionality in user interfaces like management, message passing, input processing, and standard controls. These DLLs are recorded in the registry we’ve mentioned. This registry key is worth mentioning and monitoring for malware residence.
Known DLLs
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\KnownDLLs
Modify the list of known DLLs to add a malicious DLL to load before the signed version, since Microsoft follows a search order when finding DLLs to load. This key makes sure the DLLs are known to the system and can be included from a path that’s purposefully placed before the path of the original file. This is also called “DLL Search Order Hijacking” where a malicious DLL takes place of a well-known DLL, simply because of its placement.
File Type Association
HKLM\Software\Classes\
HKEY_CLASSES_ROOT\
What happens when a text file opens? The commands are run from this CLASSES_ROOT hive as this is where the associations are kept.
Conclusion
That’s it for today folks. Like I said, there are a few more registry keys that are likely to be targeted by malware authors and adversaries. We’ll keep updating the list and make sure you’re updated with the latest list of forensics findings.
Till the next article, stay safe!